A simplex/half-duplex/full-duplex communication concept
1. Simplex communication:
Simplex communication definition: The working mode in which information can only be transmitted in one direction between two points. It means: Assuming that A and B communicate, only one party can send data to the other party and cannot receive it from the other party. Data. Just like the earpieces played by children, tie a line between the two cups and tighten it, so that you can talk to the cup and hear the sound on the other side.
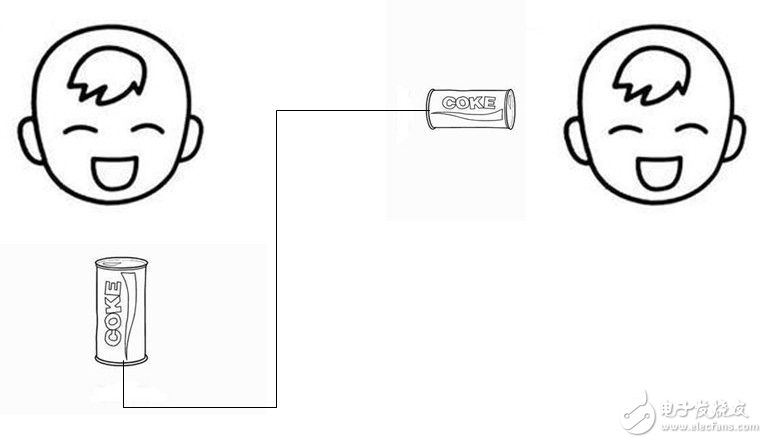
Figure 1 A child is talking to the jar while another child is listening to the audience.
2. Half-duplex communication:
Half-duplex communication definition: The information can be sent in two directions between two points, but it cannot be sent at the same time. This means that the data is sent/received in sequence, for example: A sends a data request to B. After A can only receive the return data sent from B, but A can send the data request to B immediately after receiving the data transmitted from B, and B can also send data to A.
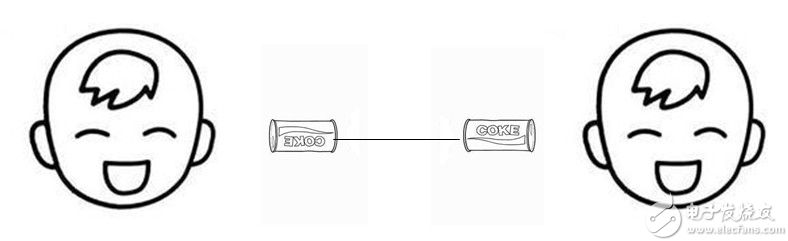
Figure 2 "Interphone" question and answer
3. Full duplex communication:
Full-duplex communication definition: Communication allows data to be transmitted simultaneously in both directions, which is equivalent to the combination of two simplex communication methods. The essential difference between full-duplex communication and half-duplex communication is that both sides of the half-duplex communication Only one line is shared to achieve two-way communication, but full-duplex communication uses two lines, one for transmitting data and the other for receiving data.
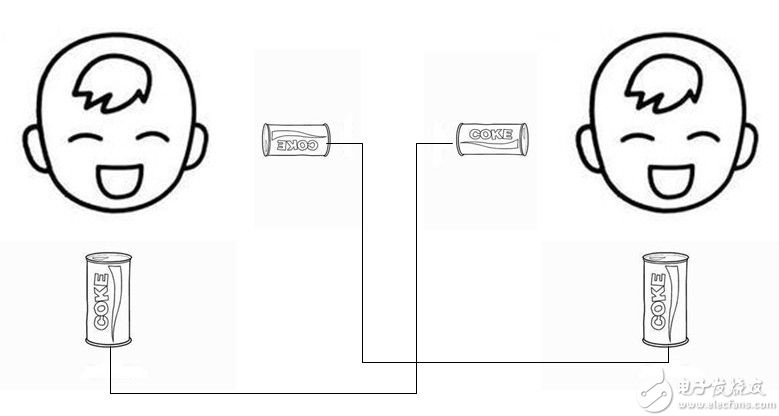
Figure 3 Model of a wired landline
Inter-chip communication
1. Serial communication:
The communication between the host and the host is essentially the transfer of data back and forth between the two chips..

Figure 4 Serial interface physical map
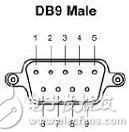
Figure 5 Serial pin sequence diagram
For the serial port interface definition of DB 9 pin: Line 2 receiving data (RxD), Line 3 transmitting data (TxD), Line 5 signal ground (GND) [The intention is to shield the external electromagnetic interference]
*RS-232 protocol design:
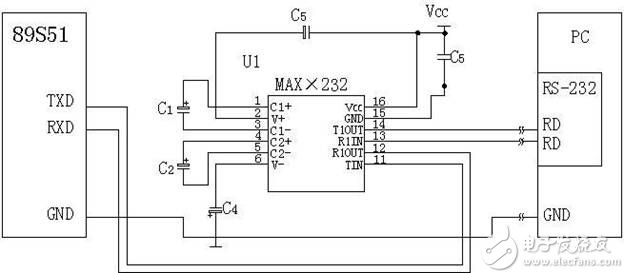
Figure 6 Communication between the 89S51 series MCU and the PC
For some chips that do not have an RS-232 output signal, the designer uses the MAX 232 (a device that converts the TTL level of the chip communication output to an RS-232 signal) to connect the PC to the chip. In Figure 6, the 89S51 first Send data to the MAX 232 T1IN through TxD, then the MAX 232 converts the TTL level signal into an RS-232 signal inside it. Finally, the MAX 232 sends it to the COM interface of the PC through T1OUT, and the PC receives the signal we sent. Data (the reverse is the receiving data: COM TxD -> R1IN -> R1OUT). Knowledge about the microcontroller can be consulted. It is easier to understand.
Three communication protocol
1. Ethernet transmission protocol:
Ethernet definition: It is widely used and uses a shared bus type transmission medium. In the past, if multiple computers want to use a Moden to access the Internet, they need to add a hub (HUB) to connect these computers in parallel. [PS : Hubs and switches (SWITCH), the hub will distribute the total network data transmission rate evenly to each computer, but the switch does not, which is related to hardware design]

Figure 7 Hub physical map (this year, looking for a picture without a watermark is really rare..)
The following is a topology diagram of multiple computers sharing network lines.
Figure 8 Bus type data transmission link
The line is shared. How does a computer in the line know whether the data in the line is sent to itself or to other computers? For this reason, an Ethernet data transmission protocol has been developed. The following figure shows the transmission data structure. .
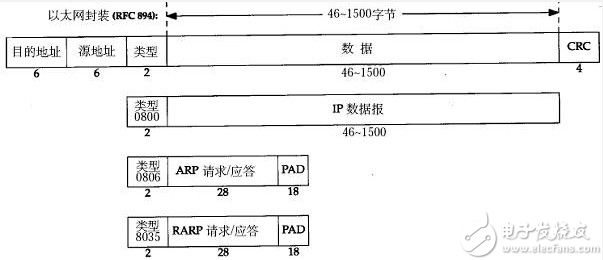
Figure 9 Ethernet data transmission structure
The destination address refers to which computer the data is received from. The source address is where the data is sent from. For example, if the host needs to send data to the WAN, then the destination address is filled in the address of the hub's network adapter. (This address is the MAC address, which is the unique address owned by the network adapter.) When the hub receives the data and forwards the B host, all hosts on the bus can receive the packet, assuming the host receives the packet. It will compare the destination address in the packet with its own network adapter. If it is the same, it means that the data is passed to me. If it is not the same, the packet will be discarded. This explains the other hosts listening to the same bus. The principle of sending/receiving network information.
There are many different types of Ethernet packets. The above are three types commonly used under hubs: IP data transmission [0x0800], ARP request/response [0x0806], RARP request/response [0x8035].
ARP Request/Reply: Its use is to initiate an inquiry on the bus using the address of a network adapter and then get the IP address of the network adapter to be queried. Since the computer needs to rely on a hub or switch or router to deliver the message, it must To use the ARP request to tell the hub, etc., the MAC address of the network adapter that forwards the message hardware. [PS: You can also use the RIP (Routing Information Protocol) protocol to obtain the IP address from the forwarding message hardware (send the MAC address of the network adapter to obtain the IP address). Address)]. After receiving the request, the forwarding message hardware will look in the ARP cache table (corresponding to the computer's IP address and the network adapter's MAC address). If there is no such MAC address, the MAC address is updated in the ARP cache table. Address, and then send an ARP reply packet, then when the forwarding message hardware receives the message, it can look up the MAC address in the ARP cache table according to the IP address in the data and then send it on the bus. If the IP of a packet is received If the address is not found in the ARP cache table, the forwarding message hardware will discard the packet and send ICMP data to the source IP address. Unreachable packets. Note that the forwarding message hardware typically refreshes the ARP cache table in thirty minutes.
RARP request/response: What if we only know the IP address of a computer under the hub and want to send data to it without the MAC address of the computer's network adapter? Then we need to broadcast RARP to the bus (reverse) Request to the address translation protocol), the destination address in the Ethernet data structure is set to FFFFFFFFFFFF (ie: -1), and the destination IP address in the RARP packet structure (see Figure 13) is set to the IP address to be queried. Next, when the network adapter of a computer under the bus receives it, it compares the IP with itself. If the IP address is queried, it returns the IP address and MAC address of the network adapter. RARP replies, finally querying the host to update the ARP cache table of the machine after receiving the packet, and then can send data of the IP layer.
Figure 10 ARP /RARP packet structure
2.IP protocol:
Since the Ethernet protocol is only applicable to LANs, and Ethernet data cannot be sent across the messaging hardware, people have developed an IP (Internet Protocol) protocol. With it, as long as the computer is connected to the Internet, it can use IP. The address (like the mobile number) is used to communicate (just like a mobile phone using the GSM protocol). Here is the IP protocol packet structure: 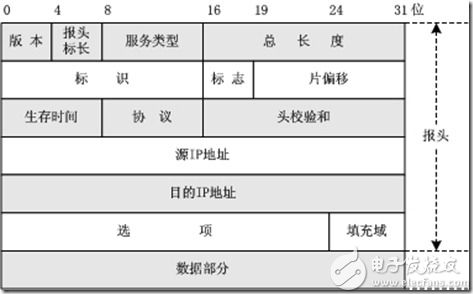
Figure 11 IP Protocol Header Packet Structure The source IP address and destination IP address have the same meaning as the source and destination addresses in the Ethernet packet structure. (Other TCP features are omitted here because they are not relevant to this document.)
Readers will take a look at the following network topology diagram:
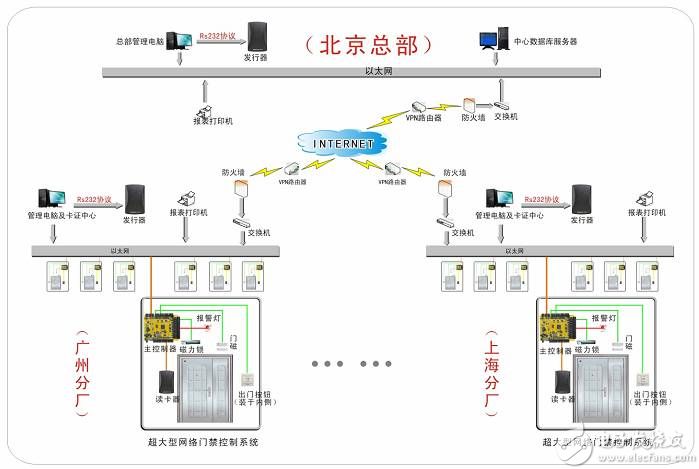
Figure 12 Network topology diagram of the network access control system
There is a main controller in each access control system. These main controllers use Ethernet to transfer data to the Internet (Internet) through the switch. Since the Ethernet transmission protocol can only be used under the same Ethernet, These data are impossible to pass outside of this area. You can think of it this way: The main controller of one of the access control systems in the Guangzhou branch sends a message to the Ethernet network it belongs to to the management computer and card of the Shanghai branch. The license center host is obviously not acceptable. The IP protocol is different. The IP (Internet Protocol) protocol is suitable for all hosts that have their own independent IP address as long as they are connected to the Internet. Therefore, when one of the access control systems of the Guangzhou branch is to be To exchange data with the management computer and card center of the Shanghai branch, you must know the IP address of the host. With it, the system will fill in the data of the IP protocol header packet according to the actual situation, and then pass Ethernet is designated to be sent to the switch. The switch will forward our packets to the Internet, and then the packet Will arrive at the switch of the Shanghai branch, and finally the switch of the Shanghai branch sends data packets to the management computer and the card center host via Ethernet.
Based on the IP protocol, we can also use TCP and UDP to transfer data to achieve data transmission. In general, TCP will provide "no difference", "reliable" data transmission services.
3.TCP protocol:
As a widely used protocol, the TCP protocol has many features that are not available in network communication protocols (such as retransmission). The TCP protocol is developed based on the IP protocol. Let's first discuss the TCP packet structure:
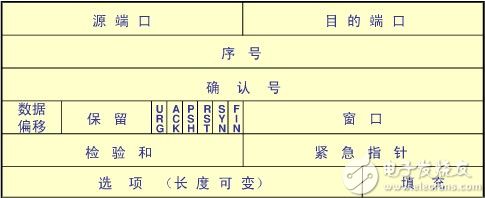
Figure 13 TCP protocol header data structure
The TCP protocol does not specify the sender/receiver's address because it is based on the IP protocol, so the IP protocol address can also be said to be the address of the TCP protocol. In the TCP protocol header data structure, there is a new one. The noun is called "port". Its purpose is to identify different programs to receive different data packets, such as: 80 ports send/receive HTTP protocol packets, 21 ports implement TELNET protocol, etc. The TCP protocol transmission mechanism is quite special. It first needs to establish a communication connection between the two hosts before it can transfer data. Finally, the connection must be closed when the data transfer is completed. First look at the following TCP communication flow chart:
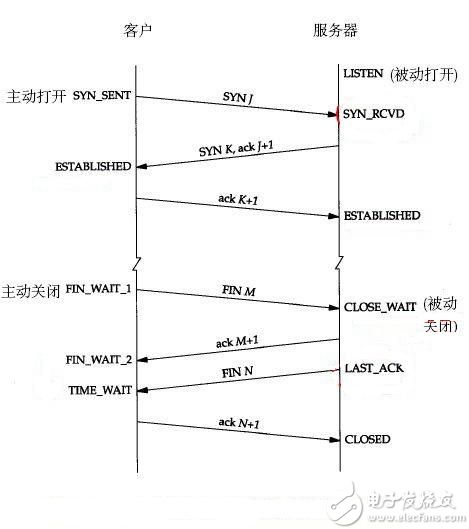
Figure 13: TCP protocol communication connection and packet transmission when the connection is closed (because the source picture is drawn a lot of red circles, there is no way to rescue it like this, forgive LC)
For the above packet exchange we can be divided into two parts to analyze: the first three packets mean to establish a TCP connection, the last four packets mean to close the TCP connection.
When TCP establishes a connection, the actively established party will send a TCP packet of type SYN_SENT to the destination host. The destination host will return the TCP packet of type SYN_ACK immediately after completing the connection request. (Editor's Note: Regardless of whether the destination host is willing or not It establishes a connection. To implement this structure, it must ignore the external influence conditions of the firewall, etc. Finally, after the actively established party receives the SYN_ACK packet, it returns an ACK packet, which also represents the successful establishment of the TCP connection. This is the TCP three-way handshake process.
When the data transfer between the two hosts is over, close the connection. When one party actively closes the connection, it will send a FIN packet to advertise the other party. After receiving the FIN packet, the other party will return the FIN_ACK packet to confirm. (Editor's note: Any host that has actively sent a FIN packet can no longer send any data, but can receive data.) Only if both parties have completed sending FIN packets, the TCP connection is closed. This is TCP. Four handshake process.
Sending data is similar to these, and interested readers can check out <> or leave a message to LCatro.
4. Small summary:
The structure of the packet is messed up? Please take a look at the picture below..
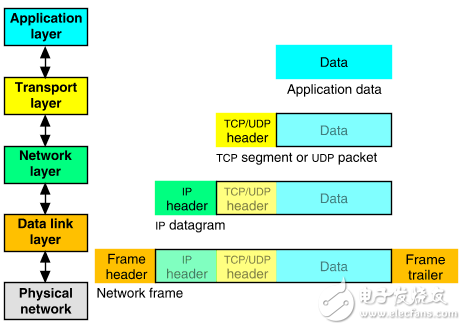
Figure 14 Network packet structure
Since we use Ethernet protocol to send data under Ethernet, our data to be sent to the destination host is included in the data of the Ethernet packet. For this data, it is actually an IP packet, but inside the IP packet. The data is actually a TCP packet. The data in the TCP packet is the information we want to send. So the readers can easily understand the network packet structure (on the right) by combining the above diagrams.
As for the structure diagram on the left, it means the network model, which represents the level of which network model layer the protocol is located in.
With the improvement of consumption level,more and more computer users and game players to computer peripherals comfort and quality put forward higher request. Once as a high-end peripherals products mechanical keyboard are no longer the exclusive of enthusiasts,
Gaming Keyboard Mechanical is the main type of game, blood hand ghost is one of the high-end mechanical keyboard.The top of the mechanical shaft with a cross design, used to button cap, there is a spring in the shaft,the spring used in different axes is not the same.the design of the shaft is not the same, this is why the mechanical keyboard has different axes, different shaft pressure countable and sound is not the same,the choice of the crowd is not the same.Mechanical keyboard can be divided into tea axis,green axis,black axis and red axis,different axis feel is also very different. Because of this mechanical keyboard of its unique mechanical structure, mechanical keyboard has a strong sense of paragraphs,which is suitable for video game entertainment special handle.so often as more expensive high-end game peripherals,among them the black shaft mechanical keyboard, because its straight on straight down the feeling of frustration and strong rebound,more suitable to use as a professional Gaming Keyboard.
Compared with the Wireless Gaming Keyboard,the mechanical keyboard hasthese advantages.Mechanical keyboard is the most important axis,mechanical keyboard than ordinary film keyboard long life,a good mechanical keyboard life of more than 10 or even 20 years.After the use of mechanical keyboard for a long time,the feel of the key changes very little,but the film can not achieve.Machinery has a different feel of different axis of the keyboard,thin film is a single touch.Mechanical keyboard can no rush,do 6 key part mechanical keyboard can all key without conflict,and more than 3 key conflict-free membrane keyboard less (therefore very suitable for the game,most professional electric campaign player will use the mechanical keyboard) to improve the level.5.You can change your own key cap, convenient personalized DIY.

Gaming Keyboard Mechanical,Slim Gaming Keyboard,Membrane Gaming Keyboard,Rgb Game Mechanical Keyboard
Henan Yijiao Trading Co., Ltd , https://www.yjusbhubs.com